
As an itinerant Hackaday writer I am privileged to meet the people who make up our community as I travel the continent in search of the coolest gatherings. This weekend I’ve made the trek to the east of the Netherlands for the ETH0 hacker camp, in a camping hostel set in wooded countryside. Sit down, connect to the network, grab a Club-Mate, and I’m ready to go!
Forget the CTF, Connecting To WiFi Is The Real Challenge!
There no doubt comes a point in every traveling hacker’s life when a small annoyance becomes a major one and a rant boils up from within, and perhaps it’s ETH0’s misfortune that it’s at their event that something has finally boiled over. I’m speaking of course about wireless networks.
While on the road I connect to a lot of them, the normal commercial hotspots, hackerspaces, and of course at hacker camps. Connecting to a wireless network is a simple experience, with a level of security provided by WPA2 and access credentials being a password. Find the SSID, bang in the password, and you’re in. I’m as securely connected as I reasonably can be, and can get on with whatever I need to do. At hacker camps though, for some reason it never seems to be so simple.
Instead of a simple password field you are presented with a complex dialogue with a load of fields that make little sense, and someone breezily saying “Just enter hacker and hacker!” doesn’t cut it when that simply doesn’t work. When you have to publish an app just so that attendees can hook up their phones to a network, perhaps it’s time to take another look .
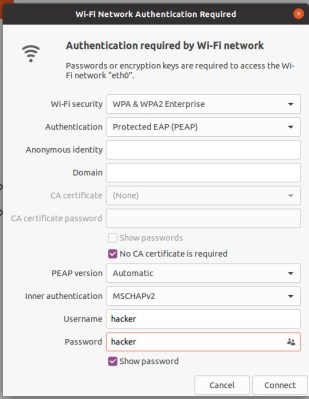
So what exactly am I complaining about and what does it all mean? Here’s a screenshot of the offending dialogue, in all its verbose glory.
At the top is a pulldown: WiFi security. This defines what type of network it is, and on my Ubuntu system it has the full range of security types from ‘None’ for an open network to “WPA3” for the most recent security standard. Most wireless networks in use today have WPA2 security, and this one is no exception. It has “WPA & WPA2 Enterprise”, which means that it follows the fancy version of WPA2 which uses a signed certificate to authenticate the access point. By contrast those other networks use “WPA Personal”, meaning that the client automatically trusts any access point following the same SSID and password combo, without requiring a certificate.
This use of WPA2 enterprise security makes sense for the security conscious administrator even if it’s annoying for the end user to configure, and as it turns out it’s the next pulldown labelled “Authentication” that’s the annoying one on my system. By default it shows “Tunnelled TLS” as its sprotocol, where it turns out that the hacker camp networks use “Protected EAP (PEAP)”. This is a protocol that protects the initial key exchange against a third party eavesdropping on packets and hijacking the connection.
The Network Giveth Security, And Then Taketh It Away
There are a few options for identity, domain, and certificate authentication servers, but the next important setting is a checkbox: “No CA certificate is required”. This is both important and infuriating, because going back to the point earlier about WPA2 Enterprise requiring a signed certificate, it appears to dispense with that entirely making the whole point of all this annoying configuration meaningless.
So if you use a protocol that requires a certificate to authenticate the access point and then do without the certificate, where is the benefit? I am no networking guru, but as far as I can see it lies in PEAP protecting my key exchange. Since my access point isn’t authenticated using a certificate there is nothing to stop a malicious third party setting up a rogue access point and capturing my connection anyway, so that benefit seems marginal.
I started this investigation from a standpoint of being annoyed at arcane WiFi set-ups, and assuming I understand the configuration correctly I have ended it unsure whether there is any benefit to the end user of having it in the first place. If you’re a wireless networking guru then please weigh in down in the comments, I’d really like to know.
Meanwhile I have a suggestion. Most camps have two networks, the WPA2 Enterprise one described above, and an open “insecure” one with no encryption and sometimes precious little between client and the wider internet. Can I suggest that they also have a network running WPA2 Personal, like every Starbucks, and leave the extra configuration for the 1337? It would save *so* much confusion!
(Editor’s note: If you’re wondering what’s up with the porta-potty full of network gear, it’s a long story. But the short version is, cheap and easy weatherproof housing.)
Header image, SHA 2017 Datenklo, Mitch Altman, CC BY-SA 2.0.
No comments:
Post a Comment